
a network engineering blog
A veteran network engineer's thoughts on packets, protocols, and all the things that should have been statically routed — including his career.

Networking Field Day 40 – Back at it again
- Tony Mattke
- Industry & events
- February 26, 2026
- 4 min read
I’m Heading to Networking Field Day 40 I’m excited to announce that I’ve been selected as a delegate for Networking Field Day 40, taking place April 8–10, 2026 in Silicon Valley. For those unfamiliar, …

Networking Field Day 40 – Back at it again
- Tony Mattke
- Industry & events
- 4 min read
I’m Heading to Networking Field Day 40 I’m excited to announce that I’ve been selected as a delegate for Networking Field Day 40, taking place April 8–10, 2026 in …

Stop using 192.168.1.0/24: A Contrarian Guide to Home Network Addressing
- Tony Mattke
- Design & architecture
- 11 min read
If you’re a contractor, consultant, or anyone who VPNs into multiple client networks, you’ve experienced the pain. You connect to a Client’s VPN, and suddenly you …
Debating SSL Decryption in 2024
- Tony Mattke
- Security
- 2 min read
Yet another day brings another meeting about another security product recommending SSL Decryption at our network edge. Your Intrusion Prevention System (IPS), your web filter, the …

Engineering a Better Blog: Our Move to Hugo
- Tony Mattke
- Homelab & misc
- 5 min read
Routerjockey has transitioned to Hugo, a fast and flexible static site generator. Hugo utilizes a straightforward, markdown-like syntax for content creation, and has a robust …

Cisco Viptela drops the ball
- Tony Mattke
- Industry & events
- 3 min read
In 2012, we saw the launch of Viptela, a pioneer in SDWAN network solutions. While they weren’t the first in SDWAN, I believe that badge goes to Talari; Viptela was the …

Will 2023 be the year of Artificial Intelligence for InfoSec?
- Tony Mattke
- Security
- 3 min read
Gartner has been saying that “next big thing” in network security is the increased use of artificial intelligence (AI) and machine learning (ML) technologies for years now… Mainly …

Introducing Graphiant: The Future of Network-as-a-Service
- Tony Mattke
- Industry & events
- 3 min read
As businesses continue to shift towards remote and distributed work environments, the need for secure and reliable network infrastructure has never been greater. Enter Graphiant, a …

Mandatory Cisco DNA Licensing – is this the Future??
- Tony Mattke
- Industry & events
- 3 min read
With the release of the new 9200 series switches many enterprise organizations are starting to look towards the future. Cisco has also been looking towards the future… of their …
AIOps the next big thing for Enterprise IT?
- Tony Mattke
- Design & architecture
- 3 min read
But how does all of this relate to IT Infrastructure and Operations? AIOps is the combination of AI and IT Operations. And while the IT community hears the AI related buzzwords, …

Gartner – more than a magic quadrant
- Tony Mattke
- Design & architecture
- 4 min read
In the past I have personally given a lot of flack towards Gartner, but that was when I was in a different stage of my career. Over the past two years I’ve transitioned into …

PCAP PCAP PCAP – Changes to RJ Store
- Tony Mattke
- Homelab & misc
- 1 min read
I made a couple changes to the RouterJockey store this week and I wanted to make sure I got the word out. Previously the store worked in sprints that I tried to open up 2-3x a …

IP Infusion powering the world from behind the scenes
- Tony Mattke
- Industry & events
- 2 min read
Founded by Kunihiro Ishiguro and Yoshinari Yoshikawa the founders of GNU Zebra, came together to form IP Infusion back in 1999 as a commercial-grade, hardware-independent …

VMware NSX is something something awesome
- Tony Mattke
- Industry & events
- 4 min read
At times I have trouble focusing on writing articles for some of the presentations I am exposed to at Tech Field Day. Because of that, I really wanted to try something different. …

PCAP t-shirts just in time for CLUS17
- Tony Mattke
- Homelab & misc
- 1 min read
Hey guys, I just wanted to drop a quick note to let you know that I’ve relaunched my teespring shirt campaigns with enough time that you should get your orders before Cisco Live US …

PNDA provides scalable and reactive network analytics
- Tony Mattke
- Industry & events
- 4 min read
During Networking Field Day 15 our friends from the Linux Foundation, including Lisa Caywood, briefed us on a recent “acquisition” from Cisco. PNDA (Panda) is an open source …

Networking Field Day 15 – A new delegate emerges
- Tony Mattke
- Industry & events
- 2 min read
Yet again I find myself honored, and questioning their selection methods, by being selected for a Networking Field Day event. Networking Field Day 15 kicks off April 6 and 7th in …

Ixia Vision ONE – Tap the Planet
- Tony Mattke
- Industry & events
- 2 min read
Whenever I start talking about network visibility and aggreagation taps I can’t help but think of The Matrix. Millions of packets flowing through your network every minute of every …

Forward Networks – A forward approach to formal verification
- Tony Mattke
- Industry & events
- 3 min read
Forward Networks has stepped out of the shadows to announce their Network Assurance platform, and I was fortunate enough to be a delegate for Networking Field Day 13 to see their …

Intel Atom SoC bricking more than Cisco products
- Tony Mattke
- Industry & events
- 2 min read
Looks like the culprit in the recent Cisco debacle is the Intel Atom “System on Chip” (SoC) that Cisco used in it’s gear. My sources within Cisco won’t give up the goods, but many …

Cisco goes public with Clock Signal Component Issue
- Tony Mattke
- Industry & events
- 2 min read
A couple months ago many engineers started hearing rumors regarding an ISR 4331 recall, and problems surrounding the device. Until this week, none of us had very good information, …

Networking Field Day 13 – Sneak Preview
- Tony Mattke
- Industry & events
- 4 min read
This is going to be a busy week for the Tech Field Day family. They have delegates en-route to Tech Field Day 12 this morning, and Wednesday the crew for Network Field day 13 …

5 important reasons you should learn scripting
- Tony Mattke
- Automation & tools
- 3 min read
Today’s IT landscape if full of software defined marketecture, and lore of a dystopian future full of network engineers that do nothing but write code. But in reality, there are …

The complexity required for robustness, often goes against robustness
- Tony Mattke
- Design & architecture
- 3 min read
In the past few months we have seen major outages from United Airlines, the NYSE, and the Wall Street Journal. With almost 5,000 flights grounded, and NYSE halting trading the cost …

Site Upgrades for September 2015
- Tony Mattke
- Homelab & misc
- 2 min read
First, I want to apologize for not doing my job. Over the past couple years I’ve let this site become slightly stagnant. I won’t attempt to make excuses, but I will say that I’m in …

RouterJockey is launching a clothing line?!?!???
- Tony Mattke
- Homelab & misc
- 1 min read
Ok maybe that title is a bit grandiose… But due to the great response I received Friday morning from the launch of the original PCAP shirt, and the IPv6 follow-up, I decided to …

PCAP or it didn’t happen…. The t-shirt!
- Tony Mattke
- Homelab & misc
- 1 min read
Some days I don’t know why I do things… But last night I was playing around with creating a PCAP meme when my friend Josh Kittle said he’d be interested in a t-shirt like that. I …

ASA v9.4 Elliptic Curve Cryptography with TLS1.2
- Tony Mattke
- Security
- 2 min read
With ASA version 9.4 Cisco has added support for Elliptic curve cryptography (ECC), which is one of the most powerful types of encryption in use today. While ECC has been in use …

Well-Known Intervals
- Tony Mattke
- Fundamentals
- 4 min read
Listed below are many events which occur on network devices at well-known intervals. The list is provided to serve as an aid while troubleshooting recurring network disruptions. …

FCC approves net neutrality rules, reclassifies broadband as a utility
- Tony Mattke
- Industry & events
- 2 min read
Today is a good day. By a 3-2 vote, the FCC has voted to adopt net neutrality rules to protect the open Internet. This plan will reclassify internet access as a Title II public …

Cisco Live 2015 – Mike Rowe Announced as Keynote Speaker
- Tony Mattke
- Industry & events
- 2 min read
Cisco just announced to the Cisco Champion community that the guest speaker for the keynote is going to be none other than …… Mike Rowe!! In case you don’t know, Mike Rowe is an …

BGP Communities
- Tony Mattke
- Routing
- 4 min read
BGP Communities has to be one of my favorite features added to the BGP protocol. As you should know by now, BGP passes several attributes between peers that help influence the BGP …

Cisco Live 2015 – Customer Appreciation Event Featuring Aerosmith!!
- Tony Mattke
- Industry & events
- 1 min read
Yes, you heard me right. Aerosmith! One of the most looked forward to social events for Cisco Live has always been the Customer Appreciation Events (CAE). Cisco rarely let’s us …

Binary Metal Guitar
- Tony Mattke
- Homelab & misc
- 1 min read
Thank you Ed for sharing the video the led me to find this video. It's a national treasure for those of us that appreciate binary. And if you appreciate metal, or music in general …
Cisco VIRL released into the wild
- Tony Mattke
- Fundamentals
- 3 min read
After much waiting from all of us, Cisco has released, on “cyber Monday” no less, VIRL. As you may remember, VIRL was the talk of CLUS 2013, and many of us have been eagerly …
The Unofficial JNCIE-ENT Prep Guide
- Tony Mattke
- Fundamentals
- 1 min read
Some of you may have heard that Jeff Fry has published his Unofficial JNCIE-ENT Prep Guide, but how many of you have purchased it yet? I’ve had the opportunity to look it over as …
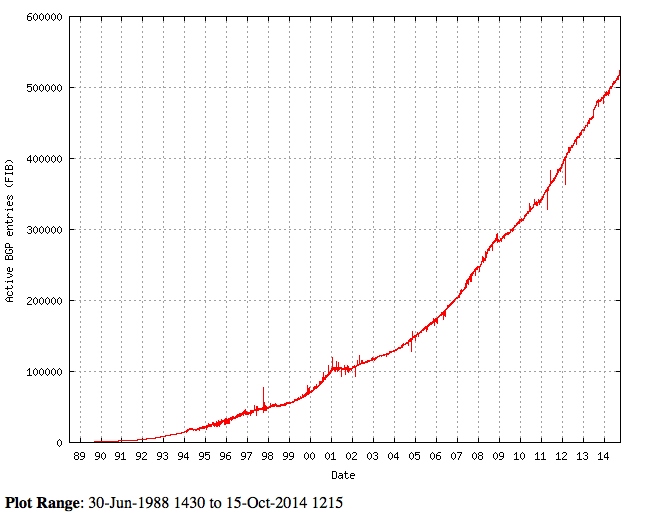
AS-Path Filtering
- Tony Mattke
- Routing
- 4 min read
Before we get into the how, let’s talk about the why. According to the CIDR Report, the global IPv4 routing table sits at about 525,000 routes, it has doubled in size since mid …

Network Design — Keeping it simple
- Tony Mattke
- Design & architecture
- 3 min read
Since the dawn of time people have skirted best practice and banged together networks, putting the proverbial square peg in the esoteric round hole. For example, new vendor XYZ’s …

Cisco ISR 4000 – Now with more licensing!
- Tony Mattke
- Industry & events
- 4 min read
This week at Interop NYC, Cisco launched it’s ISR 4000 Series. This is a new approach for them focused on delivering services to your branch offices. Cisco has dubbed this new …

HP talks SDN at Interop NYC 2014
- Tony Mattke
- Industry & events
- 2 min read
I generally try to avoid oversharing when it comes to my thoughts about presentations, but I have to mention that after sitting down with Glue Networks and their “SDN” …

Installing VMware tools on Cisco ACS
- Tony Mattke
- Fundamentals
- 7 min read
As of ACS v5.4 Cisco has finally included VMware tools for their ADE OS. Unfortunately, when you upgrade, they do not get installed automatically as the installation is triggered …

Using Deny ACEs in your PBR ACL on your Nexus 7k
- Tony Mattke
- Switching
- 1 min read
Quite a while ago I had a need for some network duct tape… Policy Based Routing while useful should only IMHO be used as a temporary fix. But as you know, temporary things soon …

Vendor PSA: Words and Phrases to Avoid in Presentations
- Tony Mattke
- Homelab & misc
- 2 min read
Over the years IT professionals have sat through countless presentations, conference calls, and keynotes. We’ve been preached too, explained “the problem”, and forced to bear …

Cisco ASA Packet Captures for Fun and Profit
- Tony Mattke
- Security
- 4 min read
As many of you know my background isn’t in enterprise, but I currently fill that role in my $job. In order to succeed I’ve had to develop many new skills including …
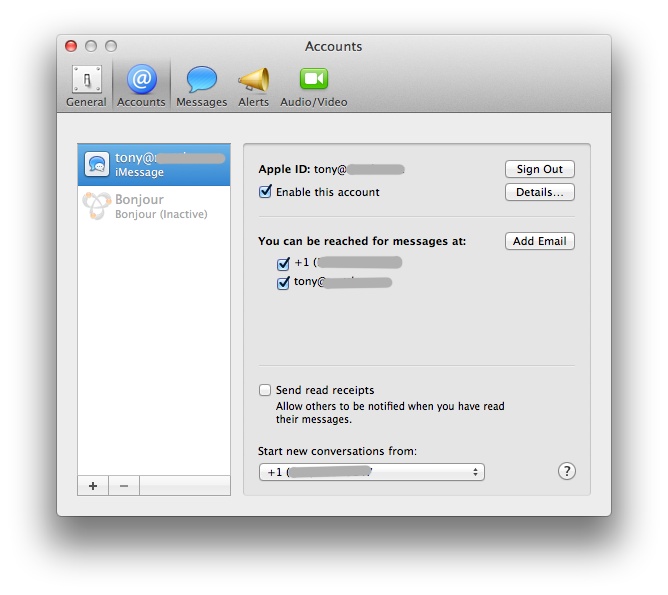
Fixing iMessage on Hackintosh
- Tony Mattke
- Homelab & misc
- 2 min read
Mid December 2012 Apple shut down the Messages Beta for Lion, soon after many hackintosh users started noticing issues with signing into iMessage. At some point in time, people far …

Double NAT – Cisco ASA 8.4+
- Tony Mattke
- Security
- 3 min read
Recently I was faced with an issue outside my normal expertise… those of you that know me realize I am anything but a security engineer. But in reality, you must always expand your …

Vim Primer for Network Engineers
- Tony Mattke
- Automation & tools
- 8 min read
Vi is arguably the best text editing software in the world. There, I said it… deal with it! It should be noted that while many people continue to refer to Vi simply as such, Vim …

Cisco Nexus 2000: A Love/Hate Relationship
- Tony Mattke
- Switching
- 4 min read
My feelings towards the Nexus 2000 Fabric Extender (FEX) are hardly a secret. The myriad of design choices and platform limitations present engineers with some rather difficult …

CCIE Potential
- Tony Mattke
- Industry & events
- 1 min read
INE published a great info-graphic on the earning potential of Cisco’s certifications and I felt the need to share it here. It covers a range of topics from average salaries on all …

QinQ: IEEE 802.1Q Tunneling
- Tony Mattke
- Switching
- 3 min read
In situations where service providers want to offer transparent LAN services that preserve a customers VLAN tags across your Layer-2 network, this amendment to the IEEE 802.1q …

Cisco IPS Fun
- Tony Mattke
- Security
- 7 min read
Since I’ve recently had some fun working with the Cisco 5585-X and the IPS blades, I wanted to document some of the information I learned while getting them online. Some of this …

Another Wicked Vim Tip
- Tony Mattke
- Automation & tools
- 6 min read
As a follow up to my blog post covering Vim on the PacketPushers blog, I wanted to share with you another time saving tip for getting our jobs done not only quickly, but helping to …

MDS Fibre Channel Switching Basics for Network Engineers
- Tony Mattke
- Fundamentals
- 5 min read
Recently I’ve been lucky enough to be challenged with learning a bit about Fibre Channel Switching, but I’m even luckier in that I’m getting to know it on a set …

Brocade and VCS… quite impressive
- Tony Mattke
- Industry & events
- 4 min read
Our second visit on day 2 of Network Field day was Brocade, who incidentally supplied us with a great lunch! We spent a little time going through the expected marketing …

Juniper QFabric, Junosphere, Automation, and More
- Tony Mattke
- Industry & events
- 4 min read
The second day of Network Field Day 2 started early at the Juniper EBC, luckily Abner Germanow was prepared with breakfast for the weary and slightly hung over delegates. He gave …

Gigamon and the Great Pumpkin
- Tony Mattke
- Industry & events
- 3 min read
I could’ve just as easily called this article Gigamon… fixing problems you didn’t know about or Why Gigamon scares the crap out of me — but I wont, because they already did! But …

NEC and ProgrammableFlow Switching
- Tony Mattke
- Industry & events
- 3 min read
NEC is currently the only Vendor that is shipping an OpenFlow enabled product today. So naturally, their presentation led off with a message about what they’re bringing to the …

Network Field Day 2 — Comic Edition
- Tony Mattke
- Industry & events
- 1 min read
During the coarse of NFD2 I found an iPhone app called Halftone, and later, one named ComicStrip that allow you to add some fun effects and speech bubbles to your photos… So, I …

Cisco Systems Awesomesauce aka Full Tilt Boogie
- Tony Mattke
- Industry & events
- 3 min read
First of all, I want to say thank you to everyone from Cisco Systems for inviting us into the CCIC (Cisco Cloud Innovation Center), this was an amazing room to hold our …

The OpenFlow Symposium
- Tony Mattke
- Industry & events
- 3 min read
Well, here is the update that I promised you. I’ve spent the last few days with some of the top minds in Networking industry. One of the most exciting technologies being presented …

Tech Field Day: OpenFlow Symposium
- Tony Mattke
- Industry & events
- 1 min read
What is OpenFlow? OpenFlow is a proposed standard for exchanging flow data between controllers and networking devices. OpenFlow has the potential to move our networking control …

BPDU the next incrementation
- Tony Mattke
- Fundamentals
- 2 min read
As I feel this may be a regular section of the blog due to my lack of availability. Please suggest a better name for this “series”. I would certainly appreciate it, as would my …

Networking Field Day 2
- Tony Mattke
- Industry & events
- 2 min read
Have you heard the news? You’re least favorite blogger is making the trip to San Jose California for Tech Field Day: Network Field Day 2 — I really want to add a dramatic movie …

SNMP can save your life
- Tony Mattke
- Automation & tools
- 3 min read
Ever get locked out of a router or switch that is many hours or even days away? Recently, I had the pleasure, again. For some reason, be it the consultant that was turning up our …

BPDU – Blog Post Data Unit?
- Tony Mattke
- Fundamentals
- 2 min read
My most recently collection of interesting bits of data found out on the blogsphere/internets. Due to my lack of time, I’ve decided to recycle what I find out on the ‘net and share …

Best Practices and Securing Cisco IOS
- Tony Mattke
- Security
- 8 min read
Everyone has different views on hardening IOS, and while I do not claim to be an expert, these are the practices that I commonly use when bringing up a new device. If you see …

Network Duct Tape Gone Wrong
- Tony Mattke
- Switching
- 4 min read
As many of you may know, I’m in the middle of a huge network redesign, last week our new firewalls finally arrived and it became time for us to start migrating services onto the …

F5’s iRules — My first look
- Tony Mattke
- Fundamentals
- 2 min read
I’ve never had the opportunity to really do much with F5 load balancers in the past, but recently one our system engineers needed some load balancing setup, and wanted to know if …

Nexus 7000 vPC Features
- Tony Mattke
- Switching
- 4 min read
Next generation data centers across the world are taking advantage of Cisco’s Virtual PortChannel. As of recent, I’ve moved our core to a pair of Nexus 7010s running …

NX-OS 5.2(1) for the Nexus 7000
- Tony Mattke
- Switching
- 2 min read
Rather quietly, at least I never heard anything, on July 29th, Cisco released NX-OS Version 5.2(1) for the Nexus 7000 platform. (and the world rejoiced) This long awaited revision …

Cisco Increases CCIE Lab Cost
- Tony Mattke
- Fundamentals
- 1 min read
This morning several CCIE candidates received an email stating that on August 1, 2011, Cisco will be raising the cost for the CCIE lab from $1,400 to $1,500. This is an interesting …

Cisco Live 2011
- Tony Mattke
- Industry & events
- 7 min read
It’s been a tough week since I left Las Vegas. I must say that my Cisco Live withdrawal has been pretty bad, and with the week we’ve been having here in Indiana, I’m certainly …

My Toolbag
- Tony Mattke
- Automation & tools
- 5 min read
Following the current popular topic of “Whats in your toolbag?” ala Stretch and Fryguy. I’ve decided (after some persuading) to detail the contents of my own bag. Without further …

IP SLA Basics
- Tony Mattke
- Automation & tools
- 3 min read
IP SLA is a function of Cisco’s IOS enabling you to analyze a Service Level Agreement (SLA) for an IP application or service. IP SLAs use active traffic-monitoring to continuously …

My Cisco Live 2011 Schedule
- Tony Mattke
- Industry & events
- 1 min read
I finished up most of my registration for Cisco Live 2011 / #cl11 yesterday and figured I would put up a copy of my schedule. My only wish would be that there was more times …

Time-based ACLs
- Tony Mattke
- Security
- 2 min read
Ever since Cisco released IOS 12.0.1T we’ve had the ability to broaden the reach of the extended ACL to allow the influence of time. Time-based ACLs reference a time range that is …

Remote Configuration Tip
- Tony Mattke
- Fundamentals
- 1 min read
I got asked a rather interested question the other day. An engineer needed to make remote configuration changes to a router, but do the commands he needed to run, he would be …

IP Multicast Routing Concepts
- Tony Mattke
- Routing
- 6 min read
Can you imagine a video conference taking place on a primarily T1 based WAN? Multiple copies of the same video stream being unicast from the host to each participant. Multiple …

Public Service Announcement for Engineers
- Tony Mattke
- Homelab & misc
- 2 min read
We all know how stressful our jobs can be. And we certainly know about our own hot button issues that press on the nerves in our brain, resulting in great pain and agony which in …

SVI Autostate
- Tony Mattke
- Switching
- 2 min read
Switch Virtual Interfaces, or SVIs on Cisco IOS use a feature called autostate to determine the interface availability. By default an SVI will show an up/down (Status / Protocol) …

Nexus 1000v – Out of Ports on a Virtual Switch?
- Tony Mattke
- Switching
- 2 min read
Yesterday, work presented an interesting issue I wanted to share with everyone. While configuring a new virtual machine one of our systems engineers was presented with an issue he …

BGP Essentials – The Art of Path Manipulation
- Tony Mattke
- Routing
- 4 min read
Most enterprise networks use BGP to peer with their Internet Service Providers if they want to be multi-homed. Many factors come into play when determining how traffic should flow, …

Introduction to the Nexus 1000V
- Tony Mattke
- Switching
- 3 min read
The Nexus 1000V is a software-based Cisco NX-OS switch that integrates into VMware vSphere 4 and operates inside the VMware ESX hypervisor. With the 1000V your virtual servers have …

OSPF Graceful Shutdown
- Tony Mattke
- Routing
- 5 min read
Striving to reach that last 9? Looking for a way to increase your uptime while still being able to do maintenance on your network? Wish you could shutdown your OSPF neighbors like …

ASA v8.4
- Tony Mattke
- Security
- 4 min read
Less than a year after changing the rules with ASA version 8.3, Cisco has released a new OS version 8.4. Since I won’t be covering the release notes word for word, you can find …

IOS Embedded Packet Capture
- Tony Mattke
- Automation & tools
- 7 min read
Tired of setting up SPAN sessions? Need to do some packet analysis? Since IOS 12.4(20)T Cisco has made Embedded Packet Capture (EPC) available. EPC is a powerful troubleshooting …

Nexus Virtual Port Channel (vPC)
- Tony Mattke
- Switching
- 4 min read
The Nexus 7000 and 5000 series have taken port-channel functionality to the next level by enabling port-channels to exist between links that are connected to different devices. …

Setting up a Cisco Access Server
- Tony Mattke
- Fundamentals
- 5 min read
Whether your networking lab has 3 devices or 30 an access server, also commonly called a terminal server, is the vital connection between you and those devices. For this purpose …

HSRP, VRRPd, and GLBP Compared
- Tony Mattke
- Routing
- 5 min read
In the world of first hop redundancy, we have plenty of choices. In order to make the right decision for your network you should know the basics regarding all three. The following …

BGP Tips! multipath load balancing
- Tony Mattke
- Routing
- 3 min read
Previous thoughts on load balancing BGP were that it is not a load balancing protocol and in order to achieve any sort of balanced traffic you would have to perform some sort of …

Petition Cisco for Educational IOS Licensing
- Tony Mattke
- Fundamentals
- 1 min read
Greg Ferro of Etheralmind.com has started a petition asking Cisco to embrace those who pursue Cisco’s certifications a legal course of licensing without the cost of building a home …

Working with the Embedded Event Manager (EEM)
- Tony Mattke
- Automation & tools
- 8 min read
Cisco IOS has plenty of gems contained within, but few are as fun, and as endlessly useful as the Embedded Event Manager, or EEM. To define it simply, EEM is a technology that …

More IOS Tips
- Tony Mattke
- Fundamentals
- 5 min read
Learning the particulars of Cisco IOS is one of the most valuable things a network engineer can do. These skills will be the basis of everything you do on the lab and on your …

Using the Cisco IOS Archive Command
- Tony Mattke
- Automation & tools
- 3 min read
The Cisco IOS archive command is not only very useful in keeping configuration archives, but it can also be used to log commands entered into the router, along with their user …

Introduction to Private VLANs
- Tony Mattke
- Switching
- 4 min read
The concepts behind Private VLANs are in fact rather simple, but it is quite easy to get discombobulated in the details. In their simplest form, PVLANs can dissociate ports within …

Bidirectional Forwarding Detection
- Tony Mattke
- Routing
- 6 min read
Bidirectional Forwarding Detection (BFD) is a UDP-based protocol that provides fast (very fast!) routing protocol independent detection of layer-3 next hop failures. BFD can be …

Measuring Cable Lengths on a Catalyst Switch
- Tony Mattke
- Switching
- 1 min read
A while back, I was playing on a 3750 switch in a customers lab and came across something I’ve never seen before. It seems that some Cisco switches have a built in …

Using Discontiguous Wildcard Masks in ACLs
- Tony Mattke
- Switching
- 5 min read
Unlike subnet masks, wildcard masks allow you to use discontiguous bits which enable you to match on a range of values. Using these within routing protocols is typically frowned …

Using Regular Expressions on Cisco IOS
- Tony Mattke
- Automation & tools
- 4 min read
As a followup to my previous post on Regular Expression Basics, I wanted to give a few examples on using them on Cisco IOS. Obviously, with a topic as large as regular expressions, …

More BGP tricks
- Tony Mattke
- Routing
- 2 min read
At times, the ‘rules of BGP’ don’t fit the needs of our productions networks. When we get into today’s production networks how often do book configurations apply? I’ll tell you one …

iPhone – Rock App Causing Devistation
- Tony Mattke
- Homelab & misc
- 3 min read
Recently, an update to all jailbroken phones could of caused major damage to anyone who uses Rock… There were several community updates in the last few days due to the iPad and new …

Cisco VOIP Basics – Call Broadcast for Cisco CME
- Tony Mattke
- Fundamentals
- 6 min read
This is the fourth and final part of my Cisco voip basics series. ( Parts 1, 2 & 3 ) Our goal in this series has been setting up a working voice gateway that you could use in …

Poor man's VPN connection
- Tony Mattke
- Security
- 2 min read
Have you ever needed to access a site that had an IP restriction, or one inside your remote network? Recently I need to access a customers remote monitoring site, but its …

Netcat – secret weapon
- Tony Mattke
- Automation & tools
- 3 min read
Netcat or nc, is a forgotten tool in too many arsenals these days. It lays dormant waiting at the command line to make connections across the globe for you. Knowing how to use it, …

Connecting Dynamips to your local network (OSX)
- Tony Mattke
- Fundamentals
- 3 min read
Ever wanted direct network access to your Dynamips lab? Have you ever needed to lab something that used the SDM, but you run Dynamips under OSX? You may have noticed using …

Policy Based Routing
- Tony Mattke
- Routing
- 3 min read
Policy based routing is the process of altering a packets path based on criteria other than the destination address, commonly referred to as ‘policy routing’. PBR (Policy …

The History of PING
- Tony Mattke
- Fundamentals
- 1 min read
Anyone that has touched a computer these days has probably heard of ping. But very few know of its true origins these days. The following is based off the original developer, Mike …

Using /31 subnets for point-to-point interfaces
- Tony Mattke
- Routing
- 2 min read
Recently a “colleague”, I use that term very loosely here, was reviewing my recommendations for changes on his network. Since they’re rather tight on public IP space, and require …

The Holy Hackintosh Build
- Tony Mattke
- Homelab & misc
- 6 min read
This is a follow up to my previous Hackintosh post chronicling the build and setup of my ‘Hack Pro’. My original goal was to build a Mac Pro clone using off the shelf parts, with …

The Road to Hack…intosh
- Tony Mattke
- Homelab & misc
- 3 min read
Over the past couple months, the lack of desktop here at home has driven me up the wall. Turning to my laptop time and time again, hooking it up to an external monitor while …

IOS ACL Resequencing
- Tony Mattke
- Security
- 4 min read
This is one of those tricks you wish you learned about 10 years ago, but never did. You know how easy it is to mess up a nice looking access list. You get one setup on the router, …

Cisco MPLS VRF Configuration and Demo
- Tony Mattke
- Routing
- 11 min read
A while back I asked everyone to vote on what topic they wanted to see next, and by no surprise almost every voted for MPLS VRFs. When I started working on this, I decided to take …

JunOS Olive Demonstration
- Tony Mattke
- Fundamentals
- 1 min read
As a follow up to my JunOS Olive tutorial, I made a demonstration video that shows Multicast functioning via OSPF to another Olive and an ImageStream VM.

Running JunOS under VMWare (updated – again!)
- Tony Mattke
- Fundamentals
- 5 min read
Interested in trying out JunOS? Can’t afford to build a real Juniper lab? Sounds like you need some Olives. No, we’re not talking about the green fruit commonly seen in a martini …

Mail Server Relay Testing
- Tony Mattke
- Automation & tools
- 4 min read
As you may know, I am not big in the server world, even less into mail servers. They make me sick. But, today I found a nifty little tool you can use to test your mail server …

Route Selection
- Tony Mattke
- Routing
- 7 min read
One of the most common questions I get concerns path selection within the router. Everyone knows (or at least they should know) that a more specific prefix will be preferred, but …

Cisco VOIP Basics – Cisco Dial Plans
- Tony Mattke
- Fundamentals
- 6 min read
This is the third part of my Cisco voip basics series. ( Parts 1, 2 & 4 ) Our goal is to help you configure a Cisco voice gateway that you could use in your home office. This …

Snow Leopard – The What It Broke Edition (updated)
- Tony Mattke
- Homelab & misc
- 2 min read
Snow Leopard was released on August 28th, and at 1:37pm I received my copy and proceeded to install it like a well trained puppy. After installing, I think I was more obsessed with …

Setting up Apple Filing Protocol and Bonjour under Debian
- Tony Mattke
- Homelab & misc
- 7 min read
Got a Mac ? Got a Linux box that you use as a file server on your home network? Sick of problems with samba? So was I, until today when I decided to figure out how to setup Apple …

Cisco VOIP Basics – Installing Cisco Call Manager Express
- Tony Mattke
- Fundamentals
- 5 min read
This is the second part of my Cisco voip basics series. ( Parts 1, 3 & 4 ) Our goal in this series is to setup a working voice gateway that you could use in your home office. …

Testing TCP Connectivity on Cisco Devices
- Tony Mattke
- Fundamentals
- 2 min read
Ever thought you might be having some Layer 4 connectivity issues? Pings as you should know are ICMP transmissions and ICMP is a Layer 3 protocol (commonly used to send error …

Cisco VOIP Basics
- Tony Mattke
- Fundamentals
- 5 min read
This is the first part of my Cisco voip basics series. ( Parts 2, 3 & 4 ) VOIP is obviously becoming a large part of networks, even now part of your CCNP requirements are basic …

Usefull OS X Eject Key Shortcuts
- Tony Mattke
- Homelab & misc
- 1 min read
Recently, I was using one of my custom short cuts and fat fingered the F12 key on my laptop… What resulted was my screen shutting off. Mystified, I began searching for standard OS …

Juniper Fast Track Program
- Tony Mattke
- Fundamentals
- 1 min read
This summer I learned about a fantastic offer from Juniper to ‘fast track’ you into a certification. They’re offering training material, and if you can pass their pre-assessment …

BGP Security Tips (updated)
- Tony Mattke
- Routing
- 2 min read
For some, BGP is a rather large obtrusive beast of a protocol that scares them half to death. This is not without good reason as BGP is not only the most important protocol running …

Configuring a Cisco Router as a Frame Relay Switch
- Tony Mattke
- Fundamentals
- 2 min read
One of the most effective lab setups uses frame relay as its primary transport method. This is a configuration that many people use and praise for its ease of setup and …

Google Voice Widget for OS X ‘s dashboard
- Tony Mattke
- Homelab & misc
- 1 min read
Seriously… Why haven’t we seen this yet? This is the perfect application for the dashboard. Send text messages to your friends / family from the comfort of your computer without …

An Essential Alias for Forgetful Engineers Like Myself (updated)
- Tony Mattke
- Automation & tools
- 1 min read
How many times a day do you issue a show command from configuration mode ? If you’re anything like me, its enough to get annoying. Luckily Cisco has given us the ability to user …

Setting up VOIP lab
- Tony Mattke
- Fundamentals
- 1 min read
This week I’ve started setting up a VOIP lab to explore the technology and when I’m done, I plan to integrate it into my home network. So far I’ve purchased the following for my …

OS X Leopard Hacks
- Tony Mattke
- Homelab & misc
- 2 min read
Here are a few settings you can change using the OS X defaults command to access some system parameters. As always, proceed with caution, and don’t mess with things of which …

Demystifying Cisco Config Register Bits
- Tony Mattke
- Fundamentals
- 1 min read
Ever accidentally set your config register to a random value that isn’t in the Cisco documentation? No? Neither have I, but one day I encountered someone on #cisco that had. So I …

Securing SSH against bruteforce attacks
- Tony Mattke
- Security
- 2 min read
This is one of the methods I’ve used in the past to secure a Linux host against brute force ssh attacks. While its not a perfect method, it does a good job of preventing 100s of …

Regular Expression Basics
- Tony Mattke
- Automation & tools
- 3 min read
Before I even get started, I want to mention that not all regular expression metacharacters are supported in every application. Keep this in mind when building your matches. …

Cisco IOS Tips and Tricks
- Tony Mattke
- Fundamentals
- 3 min read
So, I’m sure these have been posted almost on every networking blog under the sun, but who knows, right? Here are a few tips and tricks to help you move around the IOS a bit …

Working on my new lab setup
- Tony Mattke
- Fundamentals
- 2 min read
So, I purchased a couple extra routers, and a second layer3 switch from @usedciscoguy. He gave me a really good deal and I plan on purchasing a 6500 series switch from him as soon …

Layer 2 Ethernet transport over OpenVPN
- Tony Mattke
- Routing
- 1 min read
One of the things I used to deploy frequently at my previous position was transport for other ISPs and businesses. Since MPLS support is in its infancy on the Imagestream platform, …

Using OSPF to create unlicensed full duplex connections.
- Tony Mattke
- Routing
- 4 min read
Recently one of my clients asked me to help resolve an issue at an aggregation point on their network. They had several connections that converged onto a single unlicensed link on …

How does latency effect throughput?
- Tony Mattke
- Routing
- 2 min read
One of the questions I get asked several times a week by my clients is as such. While most people never associate latency with the amount of data they can send across a single TCP …

Cisco IOS Naming Conventions
- Tony Mattke
- Fundamentals
- 2 min read
As I started building this lab, I realized that I had to find a refresher course on the IOS naming conventions. They have gone through a number of revisions through the years, but …

Web Searches via Quicksilver
- Tony Mattke
- Homelab & misc
- 2 min read
Everyone does a fair amount of googling these days, but any network engineer can tell you that a quick ARIN whois search can be invalueable. I know I end up there quite often. …

Fixing Vista Partition Error Messages when using Bootcamp
- Tony Mattke
- Homelab & misc
- 1 min read
So, I had to reinstall Vista on my mac today — hadn’t touched it since I moved onto the Late 08 model… and once again, I started getting the common partition errors while Vista …

Cmd + Tab Replacement for Mac
- Tony Mattke
- Homelab & misc
- 2 min read
PullTab is no longer maintained or supported. I’ve removed broken links within this article…. I’ve never liked the Mac OS X Command Tab application specific switching style… today, …

SSH Wrapper Script
- Tony Mattke
- Automation & tools
- 1 min read
Ok — this is my first script that I’m posting here. Its a VERY simple ssh wrapper script that you can place in your path, preferably in ~/bin bash #!/bin/bash …

the road to Mac
- Tony Mattke
- Homelab & misc
- 3 min read
I’ve been pondering it for quite some time, but yes now I have switched to Mac. I purchased a new 2.5ghz, 4gb of Ram, 15″ Macbook Pro. Purchased the 320gb 7200rpm hard drive …